Security is always about a key principle of defenence in depth and wireless security is no different. In this blog, we are going to take a look at some of the key principles of security for Cisco wireless network, as well as some of the specific tools you can use.

There are three key levels in securing your wireless network, which we will explore in more detail in the sections below:
- Secure the Air: How can you ensure connection between end devices and the wireless network is secure?
- Secure the Devices: Are the devices you use to connect to the network themselves secure?
- Secure the Network: Is the underlying network, which supports the WLAN infrastructure secure?
Let’s take a deeper dive into each of these three key areas.
ASSOCIATED BLOGS:
Secure The Air
The basic principles of securing the air are to ensure you have strong encryption and authentication for your devices.
You also need to monitor the environment and Cisco Catalyst Center helps here:
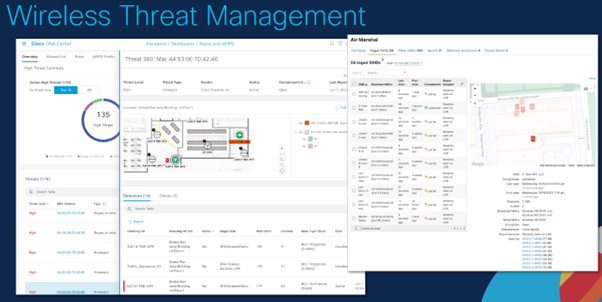
Image Courtesy of Mark Krischer, Cisco
WPA3 is the strongest encryption available and is what you should have configured on your network. For device authentication, typically you want to have two levels of accessing the network.
In most corporate networks, this means to use device certificates to authenticate and connect the device to the Wi-Fi network and then a user login to the device to gain access.
ASSOCIATED BLOGS:
Secure The Devices
.png?width=200&height=200&name=Enhancing%20Network%20Security%20Cisco%20Umbrella%20(Instagram%20Post).png) The end devices you use are of course open to attack too. Cisco has a range of tools here, which complements the Wi-Fi security toolset.
The end devices you use are of course open to attack too. Cisco has a range of tools here, which complements the Wi-Fi security toolset.
For end points you can install AMP for endpoints to protect the end point, as well as deploy Cisco Umbrella to protect the DNS lookups and optionally scan all end point traffic, including encrypted SSL traffic (it does this by working as a proxy firewall, based in the cloud).
Cisco Secure Network Analytics
The Cisco security suite also includes Secure Network Analytics (formerly StealthWatch) and the main aim of SNA is to determine when a client has done something outside of the normal pattern of its operation. Its very hard to spot a suspicious bit of activity amongst a massive amount of data, which is where SNA comes in and automates this for you.
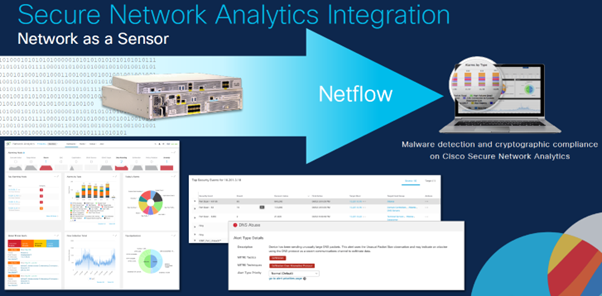
Image Courtesy of Mark Krischer, Cisco
Knowing what your devices are up to is a key aspect in securing them, so using the wireless controller as a source of netflow traffic allows you to map all these flows. Mapping the flows will show you exactly what all your clients are doing and allow you to spot any suspicious, unexpected additional flows that might be getting sent from your devices.
One method hackers use is to install their agents on an end device and then use that as a command and control station on your network – Netflow allows you to spot these unexpected flows and take action.
ASSOCIATED BLOGS:
Secure The Network
Cisco has a range of options to secure your wireless network. We’ve mentioned the obvious things such .png?width=200&height=200&name=D6%20Cisco%20Secure%20Access%20(Instagram).png) as good encryption (WPA3) and good authentication (certificates and MFA), but how about things like rogue APs?
as good encryption (WPA3) and good authentication (certificates and MFA), but how about things like rogue APs?
Umbrella and AMP help if you have clients that are roaming and connecting to hotspots, but what about the risk that someone installs an access point in your network to mimic your own APs or a threat actually gets through to your network.
Within the Cisco Wi-Fi security suite, Cisco WLCs can detect rogue APs which are mimicking your networking, or non-approved APs connected to your network and shut these down.
As part of the security suite, Cisco ISE is used to define policy and also deployed on Cisco ISE is pxGrid. Using both of these technologies, you can define policy and then apply this policy to automatically quarantine a suspected infected host to prevent it continuing to operate on your network until you have inspected it and either confirmed it ok (when you can unquarantined it), or you remediate the issues with the device.
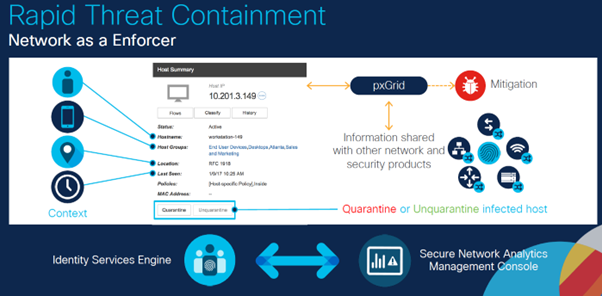
Image Courtesy of Mark Krischer, Cisco
ASSOCIATED BLOGS:
Securing your Cisco Wireless Network: Summary
The main summary from this blog is to keep the concept of defence in depth as a key aim of your security .png?width=200&height=200&name=Deploying%20Cisco%20SDA%20(Instagram).png) strategy – whether wireless of wired.
strategy – whether wireless of wired.
From a wireless perspective, we looks to secure at multiple levels and we’ve detailed how to do that at the wireless, the device and the network level. Determining when something suspicious is happening and then taking action is almost impossible for a human to filter through the vast amount of data your network is generating, which is why automated reporting and enforcement tools are required.
Automated tools mean you can set policy – and the network take care of when a suspicious flow or activity occurs, to automatically run an enforcement.
If you need any help with your Cisco Umbrella implementation, we can help.




.gif)